| Tutorial details | |
|---|---|
| Difficulty | Advanced (rss) |
| Root privileges | Yes |
| Requirements | openssl |
| Estimated completion time | 15m |
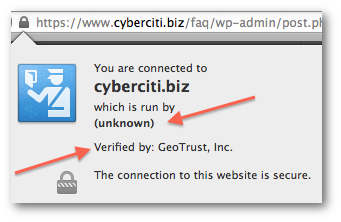
The ssl encrypts your connection. For example, a visit to https://www.cyberciti.biz/ result into the following:
- All pages were encrypted before being transmitted over the Internet.
- Encryption makes it very difficult to unauthorized person to view information traveling between client browser and nginx server.
A note about a self-signed certificates vs a third party issued certificates
- Usually, an SSL certificate issued by a third party. It provides privacy and security between two computers (client and server) on a public network by encrypting traffic. CA (Certificate Authorities) may issue you a SSL certificate that verify the organizational identity (company name), location, and server details.
- A self-signed certificate encrypt traffic between client (browser) and server. However, it can not verify the organizational identity. You are not depend upon third party to verify your location and server details.
Our sample setup
- Domain name: theos.in
- Directory name: /etc/nginx/ssl/theos.in
- SSL certificate file for theos.in: /etc/nginx/ssl/theos.in/self-ssl.crt
- ssl certificate key for theos.in: /etc/nginx/ssl/theos.in/self-ssl.key
- Nginx configuration file for theos.in: /etc/nginx/virtual/theos.in.conf
Step #1: Make sure SSL aware nginx installed
Simply type the following command to verify nginx version and feature:
Sample outputs
$ /usr/sbin/nginx -VSample outputs
nginx version: nginx/1.4.3
built by gcc 4.4.7 20120313 (Red Hat 4.4.7-3) (GCC)
TLS SNI support enabled
configure arguments: --prefix=/etc/nginx --sbin-path=/usr/sbin/nginx --conf-path=/etc/nginx/nginx.conf
...
....
..
If nginx is not installed, type the following command to download and install nginx using yum command:
See how to install Nginx web server On CentOS Linux 6 or Red Hat Enterprise Linux 6 using yum command for more information.
# yum install nginxSee how to install Nginx web server On CentOS Linux 6 or Red Hat Enterprise Linux 6 using yum command for more information.
Step #2: Create a directory
Type the following mkdir command to create a directory to store your ssl certificates:
# mkdir -p /etc/nginx/ssl/theos.in
Use the following cd command to change the directory:
# cd /etc/nginx/ssl/theos.inStep #3: Create an SSL private key
To generate an SSL private key, enter:
OR better try 2048 bit key:
Sample outputs:
# openssl genrsa -des3 -out self-ssl.key 1024OR better try 2048 bit key:
# openssl genrsa -des3 -out self-ssl.key 2048Sample outputs:
Generating RSA private key, 1024 bit long modulus ...++++++ ...............++++++ e is 65537 (0x10001) Enter pass phrase for self-ssl.key: Type-Your-PassPhrase-Here Verifying - Enter pass phrase for self-ssl.key: Retype-Your-PassPhrase-Here
Warning: Make sure you remember passphrase. This passphrase is required to access your SSL key while generating csr or starting/stopping ssl.
Step #4: Create a certificate signing request (CSR)
To generate a CSR, enter:
Sample outputs:
# openssl req -new -key self-ssl.key -out self-ssl.csrSample outputs:
Enter pass phrase for self-ssl.key: Type-Your-PassPhrase-Here You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:IN State or Province Name (full name) []:Delhi Locality Name (eg, city) [Default City]:New Delhi Organization Name (eg, company) [Default Company Ltd]:nixCraft LTD Organizational Unit Name (eg, section) []:IT Common Name (eg, your name or your server's hostname) []:theos.in Email Address []:webmaster@nixcraft.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Step #5: Remove passphrase for nginx (optional)
You can remove passphrase from self-ssl.key for nginx server, enter:
Sample outputs:
# cp -v self-ssl.{key,original}
# openssl rsa -in self-ssl.original -out self-ssl.key
# rm -v self-ssl.originalSample outputs:
Enter pass phrase for self-ssl.original: Type-Your-PassPhrase-Here
writing RSA key
Step #6: Create certificate
Finally, generate SSL certificate i.e. sign your SSL certificate with your own .csr file for one year:
Sample outputs:
# openssl x509 -req -days 365 -in self-ssl.csr -signkey self-ssl.key -out self-ssl.crtSample outputs:
Signature ok subject=/C=IN/ST=Delhi/L=New Delhi/O=nixCraft LTD/OU=IT/CN=theos.in/emailAddress=webmaster@nixcraft.com Getting Private key
Step #7: Configure the Certificate for nginx
Edit /etc/nginx/virtual/theos.in.conf, enter:
The general syntax is as follows for nginx SSL configuration:
# vi /etc/nginx/virtual/theos.in.confThe general syntax is as follows for nginx SSL configuration:
server {
listen 443;
ssl on;
ssl_certificate /path/to/self-ssl.crt;
ssl_certificate_key /path/to/self-ssl.key;
server_name theos.in;
location / {
....
...
....
}
}
Here is my sample config for theos.in:
server {
###########################[Note]##############################
## Note: Replace IP and server name as per your actual setup ##
###############################################################
## IP:Port and server name
listen 75.126.153.211:443;
server_name theos.in;
## SSL settings
ssl on;
ssl_certificate /etc/nginx/ssl/theos.in/self-ssl.crt;
ssl_certificate_key /etc/nginx/ssl/theos.in/self-ssl.key;
## SSL caching/optimization
ssl_protocols SSLv3 TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers RC4:HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
keepalive_timeout 60;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
## SSL log files
access_log /var/log/nginx/theos.in/ssl_theos.in_access.log;
error_log /var/log/nginx/theos.in/ssl_theos.in_error.log;
## Rest of server config goes here
location / {
proxy_set_header Accept-Encoding "";
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-By $server_addr:$server_port;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503 http_504;
## Hey, ADD YOUR location / specific CONFIG HERE ##
## STOP: YOUR location / specific CONFIG HERE ##
}
}
Step #8: Restart/reload nginx
Type the following command
Sample outputs:
# /usr/sbin/nginx -tSample outputs:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
To gracefully restart/reload nginx server, type the following command:
OR
OR
# /etc/init.d/nginx reloadOR
# /usr/sbin/nginx -s reloadOR
# service nginx reloadStep #9: Open TCP HTTPS port # 443
Type the following command to open port # 443 for everyone:
Save new firewall settings:
See how to setup firewall for a web server for more information.
# /sbin/iptables -A INPUT -m state --state NEW -p tcp --dport 443 -j ACCEPTSave new firewall settings:
# service iptables saveSee how to setup firewall for a web server for more information.
Step 10: Test it
Fire a browser and type the following url:
https://theos.in/
Sample outputs:
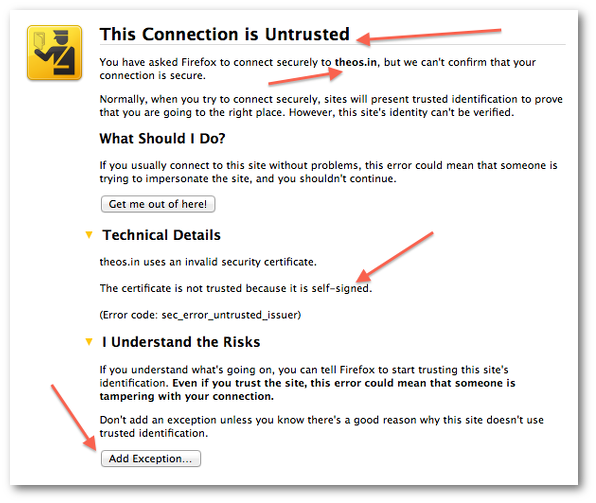
Fig.02: SSL connection is not verified due to self-signed certificate. Click the "Add Exception" button to continue.
Step 11: Verify SSL certificats
You can verify SSL Certificate using the following command:
# openssl verify pem-file
# openssl verify self-ssl.crtSEE ALSO
- See how to verify and diagnosis SSL certification installation from a Linux / UNIX shell prompt.
- Man pages: openssl(1), nginx(8)