Shell In A Box (pronounced as shellinabox) is a web based terminal emulator created by Markus Gutschke. It has built-in web server that runs as a web-based SSH client on a specified port and prompt you a web terminal emulator to access and control your Linux Server SSH Shell remotely using any AJAX/JavaScript and CSSenabled browsers without the need of any additional browser plugins such as FireSSH.
In this tutorial, I describe how to install Shellinabox and access remote SSH terminal using a modern web browser on any machine. Web-based SSH is very useful when you are protected with firewall and only HTTP(s) traffic can get through.
Installing Shellinabox on Linux
By default, Shellinabox tool is included on many Linux distributions through default repositories, includingDebian, Ubuntu and Linux Mint.
Make sure that your repository enabled and available to install Shellinabox from the that repository. To check, do a search for Shellinabox with the “apt-cache” command and then install it using “apt-get” command. `
On Debian, Ubuntu and Linux Mint
On RHEL, CentOS and Fedora
On Red Hat based distributions, you need to first have enable EPEL repository and then install it using the following “yum” command. (Fedora users don’t need to enable EPEL, it’s already a part of Fedora project).
Configuring Shellinabox
By default, shellinaboxd listens on TCP port 4200 on localhost. For security reason, I change this default port to a random (i.e. 6175) to make it difficult for anyone to reach your SSH box. Also, during installation a new self-signed SSL certificate automatically created under “/var/lib/shellinabox” to use HTTPS protocol.
On Debian, Ubuntu and Linux Mint
On RHEL, CentOS and Fedora
Starting Shellinabox
Once you’ve done with the configuration, you can start the service by issuing following command.
On Debian, Ubuntu and Linux Mint
On RHEL and CentOS
On Fedora
Verify Shellinabox
Now let’s verify whether Shellinabox is running on port 6175 using “netstat” command.
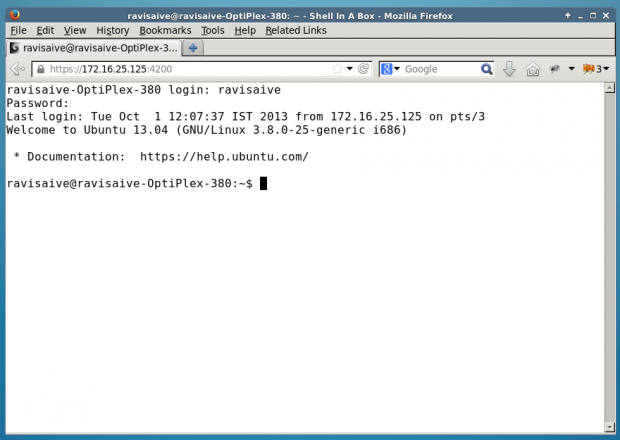
Now open up your web browser, and navigate to https://Your-IP-Adress:6175. You should be able to see a web-based SSH terminal. Login using your username and password and you should be presented with your shell prompt.
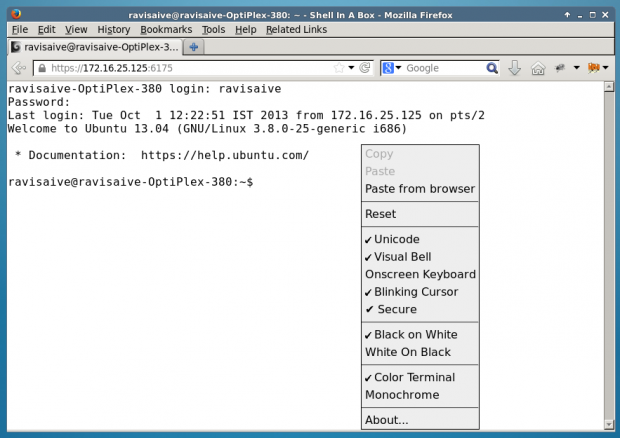
You can right-click to use several features and actions, including changing the look and feel of your shell.
Make sure you secure you shellinabox on firewall and open 6175 port for specific IP Address to access your Linux shell remotely.
Source: http://www.tecmint.com/shell-in-a-box-a-web-based-ssh-terminal-to-access-remote-linux-servers/